In a significant development that is rippling through the cybersecurity community, a critical vulnerability has been identified in ConnectWise’s ScreenConnect software (specifically versions 23.9.7 and earlier). This software is a cornerstone for many Managed Service Providers (MSPs) allowing them to administer customer endpoints worldwide. It has been assigned the highest severity rating of CVSS 10, meaning that this vulnerability poses a direct threat to the security of tens of millions of endpoints, necessitating immediate and decisive action.
Examination of the Vulnerability
Authentication Bypass Weakness
The vulnerability within ScreenConnect stems from an authentication bypass weakness. This critical flaw is a low-complexity attack that doesn’t require user interaction which permits attackers to circumvent authentication mechanisms to gain unauthorised access, with the potential to execute arbitrary code on the compromised servers remotely. This vulnerability impacts both on-premises/self-hosted deployments and cloud-based versions. Although ConnectWise has addressed the issue in cloud-hosted services (screenconnect.com and hostedrmm.com), there have been reports indicating that some cloud customers have not received automatic updates or direct communication from the company. This security lapse was brought to light on February 13, 2024, with a corrective patch released on February 19, 2024 . Nonetheless, the emergence of a proof-of-concept exploit by February 21, 2024 signals ongoing and active exploitation attempts.
Understanding Authentication Bypass Weakness
An authentication bypass weakness allows threat actors to sidestep the security measures designed to verify the identity of users attempting to access a system. This type of vulnerability can leave systems open to unauthorised access and control, creating a gateway for further malicious activities, including data theft and system manipulation.
The Risks and Implications
Confirmed by security researchers, including the team at Huntress, the vulnerability facilitates server-side remote code execution (RCE). This not only compromises the integrity of the ScreenConnect server but also enables attackers to extend their reach to connected endpoints. Given ScreenConnect’s capability to manage extensive networks of up to 150,000 endpoints, the potential scale of the impact is considerable. MSPs, which predominantly cater to the IT needs of small and medium-sized businesses, could find more than 11.4 million endpoints at risk, underscoring the critical nature of this security flaw.
Exploring Remote Code Execution
Remote Code Execution (RCE) is a security breach that allows an attacker to run arbitrary code on a victim’s system remotely, when an unsafe user supplied data is passed by the application. This capability can lead to complete control over the compromised system, enabling the attacker to manipulate data, install malware, and propagate the attack to connected systems.
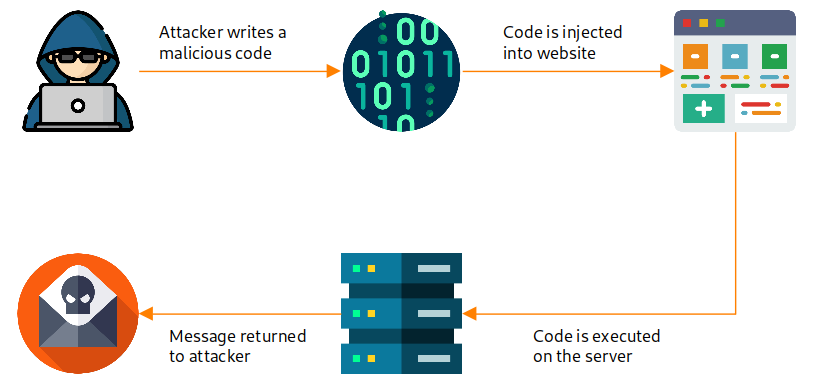
|
| Image 1: How RCE vulnerabilities work |
Proactive Measures and Response
In response to this discovery, ConnectWise released updates to mitigate the vulnerability and engaged with Cybersecurity and Infrastructure Security Agency (CISA) to facilitate widespread notification and patch adoption among its clientele. Despite these efforts, it has been reported that communication gaps have left some MSPs uninformed and unprepared, with incidents of administrative account lockouts and anomalous server behaviour indicating potential exploitation. It is strongly recommended that any ConnectWise users undertake thorough assessments of their systems to identify and rectify potential breaches.
The Need for Immediate Action
The simplicity with which this vulnerability can be exploited, coupled with the significant risks it poses, underscores the urgent need for all affected entities to bolster their defences. This includes promptly updating to the latest ScreenConnect version, vigilantly monitoring for signs of compromise, and ensuring comprehensive coverage of all potential attack vectors. The identification of thousands of susceptible servers via platforms like Censys and Shodan highlights the extensive nature of this threat.
As of 21st February 2024, there are at least 67 instances of ConnectWise ScreenConnect active in Ireland (according to Shodan.io), and only 1 of these appears to have the recommended patch applied.
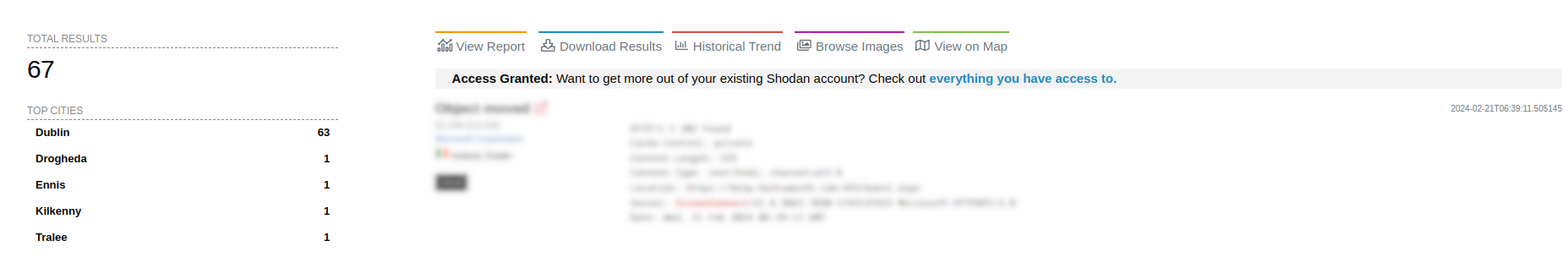
|
| Image 2: Potentially vulnerable websites in Ireland |
Observing a Disturbing Trend
This incident is indicative of a broader, more concerning trend wherein attackers exploit legitimate remote monitoring and management software for nefarious purposes. Such tactics enable adversaries to circumvent traditional security measures, facilitating unauthorised access and the potential for extensive network compromise. Recent advisories from leading security agencies have spotlighted the growing misuse of tools like ScreenConnect, emphasising the critical necessity for heightened security awareness and preventive measures.
Conclusion
The vulnerability within ConnectWise ScreenConnect emphasises a critical threat to organisations leveraging this technology for remote management. This vulnerability’s potential for broad exploitation and cause significant damage demands an immediate, thorough response. Incorporating regular vulnerability assessments and penetration testing into cybersecurity protocols can play a pivotal role in identifying and mitigating such vulnerabilities before they can be exploited.
These proactive measures, alongside informed vigilance, prompt application of critical security updates, regular patching cycles, and strict adherence to cybersecurity best practices, empower organisations to protect against this and future vulnerabilities effectively. By establishing a routine for scanning, assessing, and addressing security weaknesses, organisations can enhance the security and integrity of their systems and data, thereby maintaining resilience against the evolving landscape of cyber threats.
If you would like to discover how Secora Consulting can assist you in keeping your business secure, please get in touch by filling out the form below 👇.

